Disclaimer: I am a VERY emotional person. For some reason, great talks and smart ideas make me absurdly excited. So… sorry in advance if I’m annoying or cringy. 🙂
I had to miss Troopers this year. And honestly? It hurt. Troopers is my favorite conference. I’m pretty sure I even got to where I am in my career because of a Troopers talk I watched back in 2022 that literally changed my life.
Since the conference ended, I’ve been refreshing their YouTube page every week like some kind of obsessed person, waiting for this year’s recordings.
And last week… it finally happened!
As I watched the first talk I realized how many clever techniques and cool ideas were hidden inside. So I decided to summarize them for myself — and to share them here. This way, I can at least pretend I was some small part of Troopers25. 😀
This post includes summaries of three talks, and I’ll write about the rest in the next part.
Talks I’m covering:
- Finding Entra ID CA Bypasses – The Structured Way — Dirk-Jan Mollema & Fabian Bader
- The Ultimate Guide for Protecting Hybrid Identities in Entra ID — Dr. Nestori Syynimaa
- Hopping Across Devices – Expanding Lateral Movement through Pass-the-Certificate — Yuya Chudo
Talk 1 — Hopping Across Devices (Pass-the-Certificate revived!)
This talk didn’t just teach me something — it fixed a personal pain point.
A while ago, I tried implementing the Pass-The-Certificate attack by Mor Rubin (BlackHat 2022). It didn’t work for me, I gave up (not proud of that, but it wasn’t critical at the time).
Yuya explained exactly why the technique doesn’t work anymore:
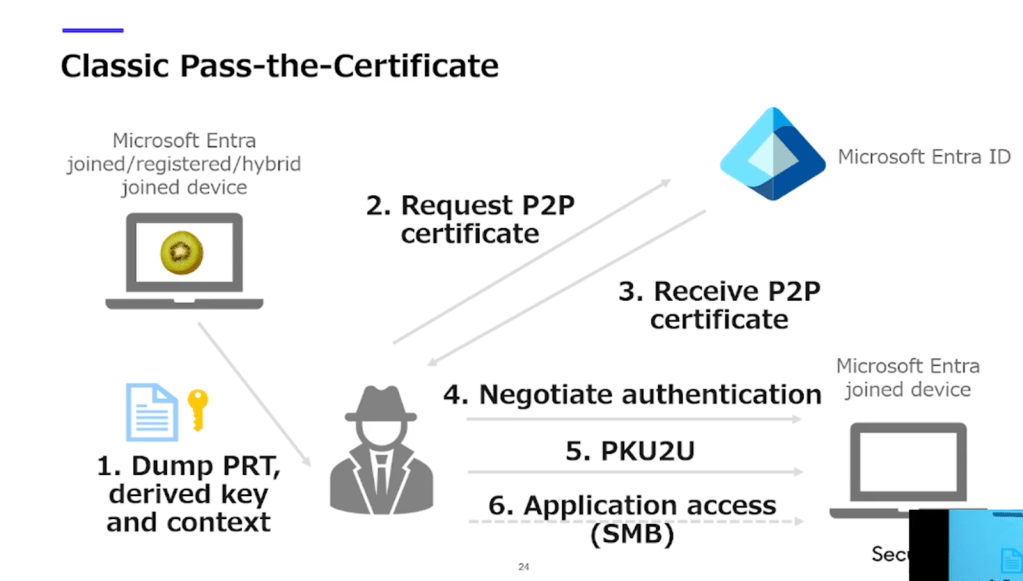
Requesting a P2P certificate using a dumped PRT + context + key no longer works.
Yuya’s talk is basically: How to weaponize Pass-The-Certificate again.
If you didn’t watch Mor Rubin’s original talk, here’s the TL;DR:
If you land on a joined device, PKU2U lets you use a device certificate to move laterally to another joined device.
Now here’s Yuya’s twist:
Don’t rely on the victim’s device. Join your own device.
If you join your own device, it’s trivial to get the key, request a PRT, etc.
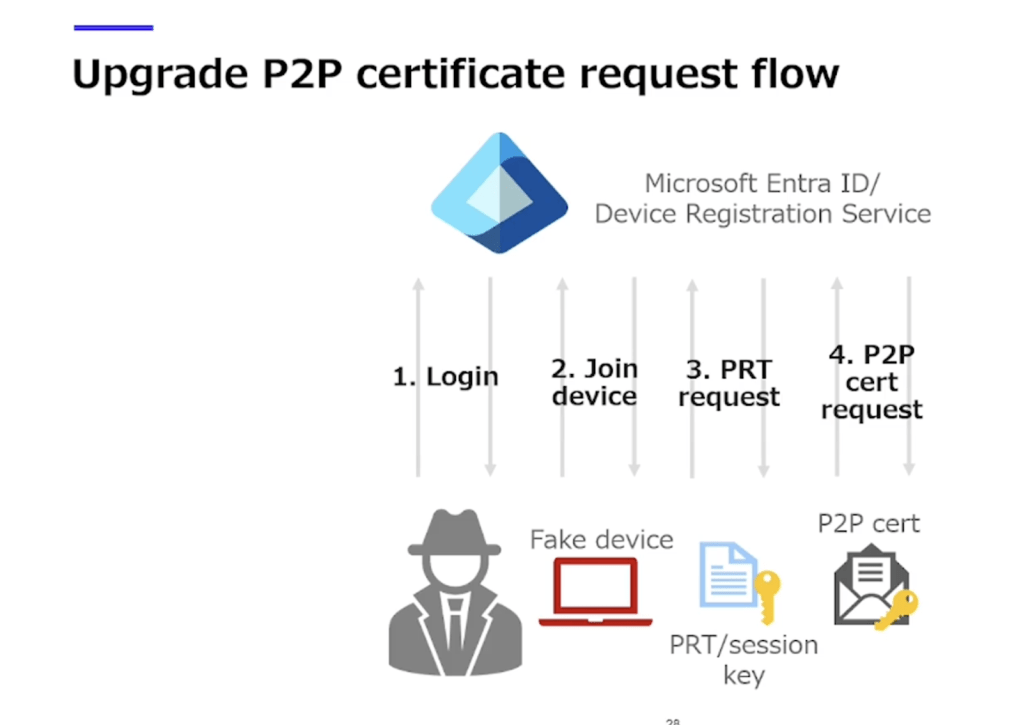
We all know by now that joining devices is easy if you have user credentials — ROPC + device registration service.
Unless the organization has a CAP requiring MFA on device registration.
To get around that, Yuya suggested two options:
- Device Code Phishing → gives you a JWT containing
mfaclaim, so you can register your device even when MFA is required. - Run malware on the device → request a P2P certificate, exfiltrate it, and use it for lateral movement.
This is simply brilliant. Yuya took a dead technique and brought it back to life — and automated it into a tool:
👉 https://github.com/temp43487580/EntraPassTheCert
The tool supports all three scenarios he presented.
He even implemented the lateral movement part (RDP or WinRM), which basically covers everything red teams need.
I’m very excited to test this and figure out detection logic. Lateral movement in hybrid environments is so hard — the attack is in Entra, but the logs live mostly on-prem. I hope to share logs and detections in the future (if Azure logs even show anything… lol).
Detection tip (even before trying it):
Please write detections for suspicious device registration authentication:
- one using ROPC
- one using Device Code Flow
There are pre-made KQL queries in this article: https://www.wiz.io/blog/recent-oauth-attacks-detection-strategies
Overall: 10/10. PKU2U is complicated, and I watched this talk at 7 AM before coffee and still enjoyed every second.
Also — Yuya has other great talks worth watching:
https://www.youtube.com/watch?v=YX5P99JUwlw
https://www.youtube.com/watch?v=JItnI6b9DII
Talk 2 — Conditional Access Bypass (a research goldmine)
This one is close to my heart because it touches the exact topics I’ve been researching lately.
This talk is PACKED with techniques, research ideas, detections, and even KQL. Some highlights:
- Using customer sign-in logs to discover additional first-party apps
- Automating authentication attempts across hundreds of apps to find misconfigurations
- Spotting successful sign-ins followed by failed CAPs – KQL!
The idea behind the detection is simple:
Find sign-ins that succeeded even though a CAP failed.
It doesn’t always mean bypass — sometimes it’s intentional — but it’s a great hunting signal.
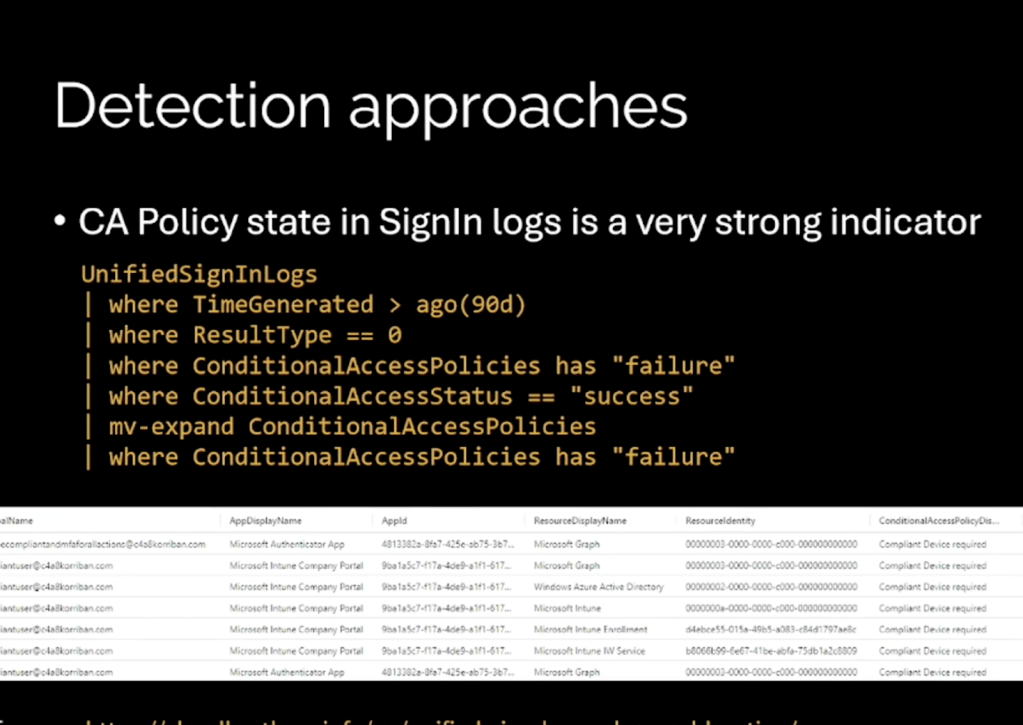
For example, I found many cases where the CAP restriction was RequireCompliantApp, which isn’t as exciting, but still interesting.
The talk also explains critical concepts extremely clearly:
- Application types
- First-Party & FOCI apps
- And the “new” family: NAA apps (aka BRoCI 😄)
SpecterOps has a great blog on that: https://specterops.io/blog/2025/10/15/naa-or-broci-let-me-explain/
One of my favorite parts: scope-based bypasses.
In some cases, requesting specific scopes causes certain CAPs not to apply. This is huge.
Honestly, summarizing this talk is hard because it’s not just the conclusions — it’s the research process. So here are my personal takeaways:
- When something doesn’t work the first time, KEEP GOING.
They tried many things. Some failed. Those failures led them to smarter techniques.
I usually lose confidence and give up after the first failure. - I’m not the only person who gets excited thinking I found something, tells everyone, and then discovers 20 minutes later that it doesn’t work.
- Good research requires patience. They automated tests, ran them overnight, and analyzed results the next day.
(Honestly the highest form of self-discipline.) - AUTOMATE. Build tools. Stop doing everything manually.
Also — they found two new FOCI clients 👀
And several app/resource combinations where CAP simply… doesn’t apply.
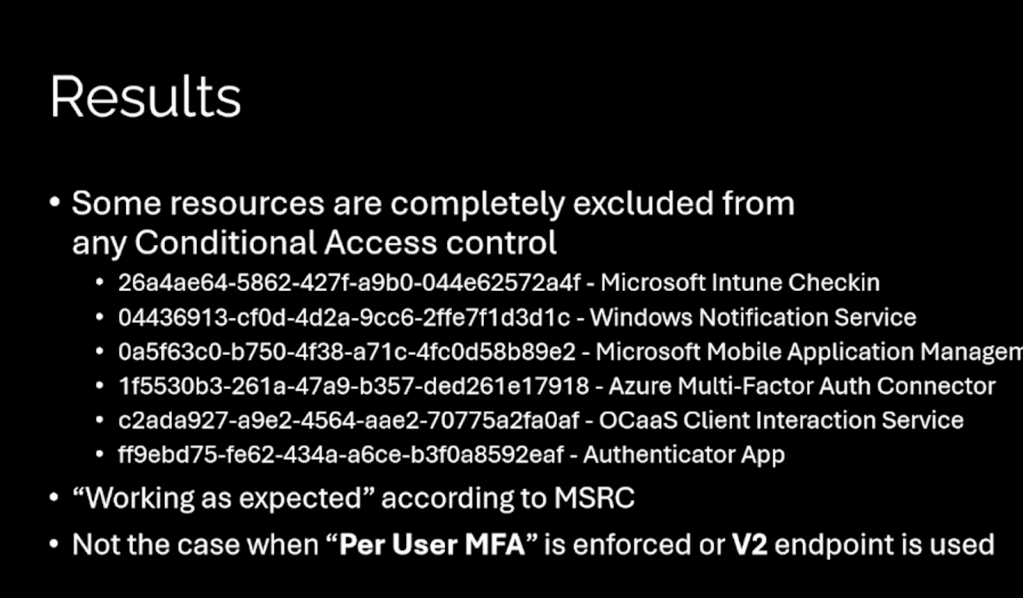
To summarize:
This talk is a sea of research ideas. The technical content is excellent, but the research mindset behind it is what inspired me the most. I feel like I got a peek behind the curtain of how real researches investigate Entra.
Talk 3 — Hybrid Identity (Nestori being Nestori)
Talks by Nestori are always half tech / half comedy show, and this one is no different.
He covers three hybrid scenarios, and for each one explains:
- Attacks
- Defenses
- And includes mitigation tables (you should copy those into your environment ASAP)
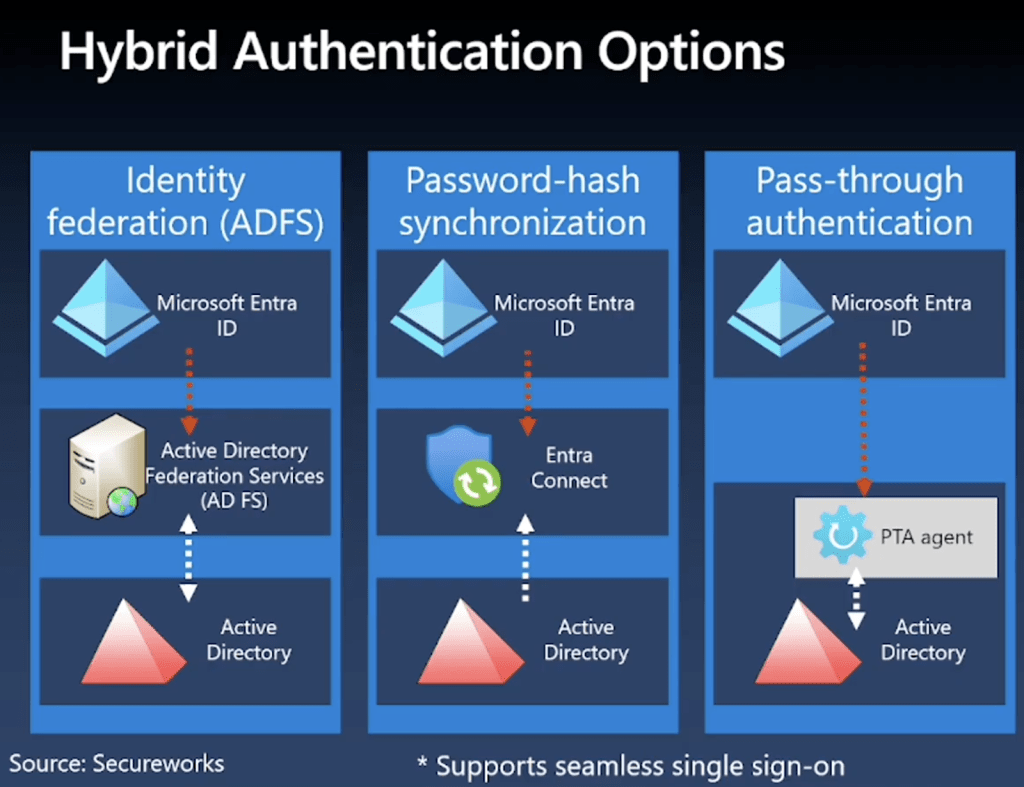
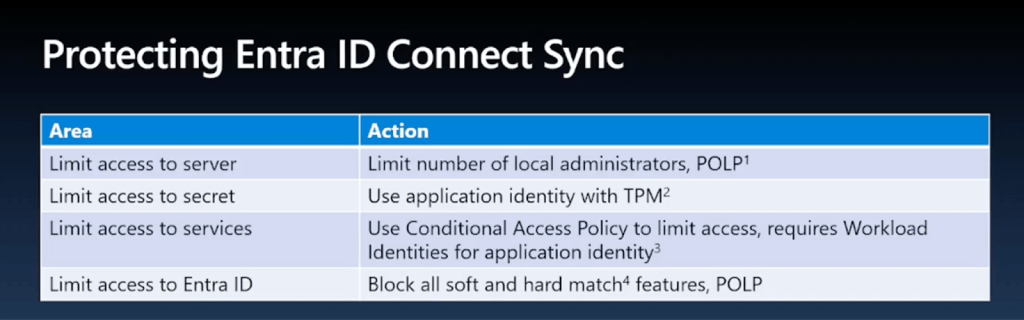
He focuses heavily on the Entra Connect account, which changed recently from user+password to an application with a certificate. Using AADInternals, he shows how to extract the certificate or secret — except in one TPM-based scenario.
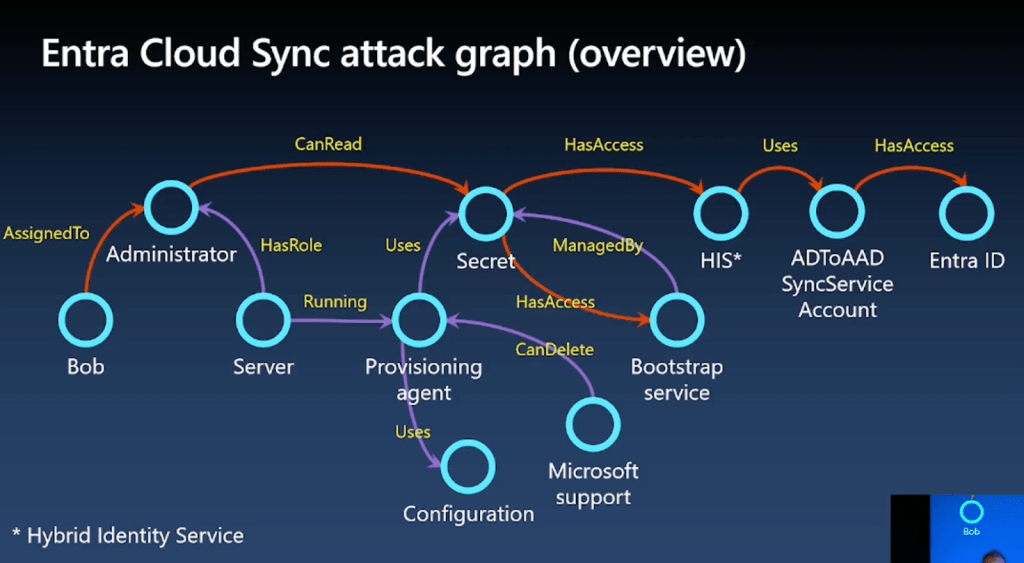
Another thing I loved: thinking in graphs.
Every attack path is illustrated as a graph, and IMO it makes everything far clearer. Especially for hybrid — which is usually confusing.
He also talks about Cloud Sync (which doesn’t get enough attention). It uses the Entra Cloud Provisioning Agent instead of the Entra Connect application. Meaning:
the attack becomes steal the agent creds, not steal the connect creds. 😀
One funny moment:
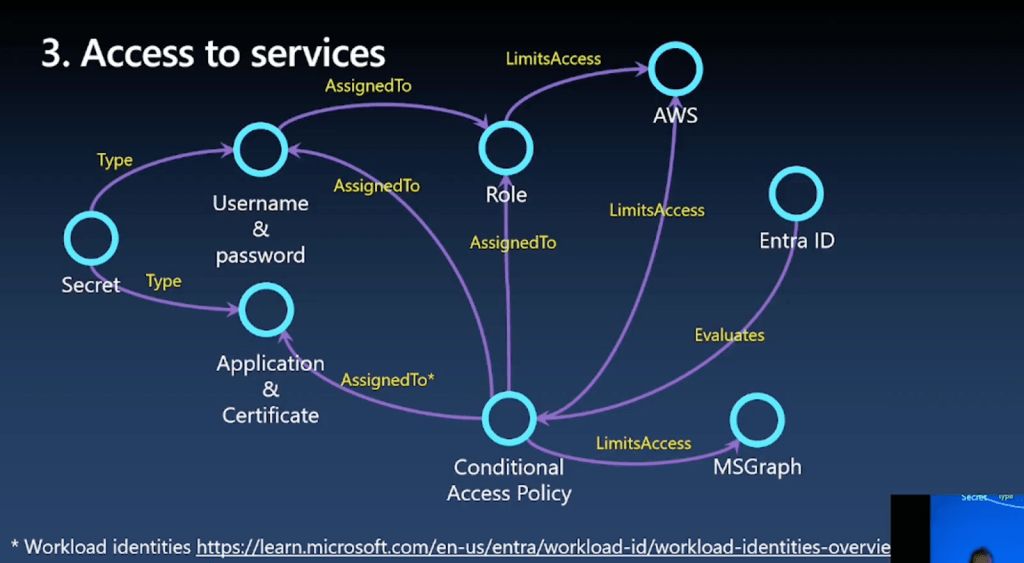
He wrote “AWS” (Admin Web Service) and for a second I thought he meant Amazon. If you work multi-cloud like me — you probably made the same mistake.
But that actually made me think:
I really want a talk about federation from Entra to AWS (Amazon).
Attackers absolutely use that technique. Maybe it’s time for Entra and AWS researchers to collaborate. Maybe I’ll be the one to start that!
Summary:
Fun, light, surprisingly beginner-friendly, and still valuable for advanced researchers.
Final Thoughts
That’s it for now. I still have more talks to watch, but Troopers25 already looks incredible (I’m still processing my FOMO).
These talks genuinely excited me — not only because of the Entra technical insights, but because they reminded me how much I love research. How much I still need to improve. And how some problems I ran into were solvable… I just needed a bit less self-doubt.
Leave a comment